如同每個故事的起頭都有個壯烈的故事一樣,去年的四月在一次壓線過 CKA 之後覺得今年對於 CKS 的準備肯定式輕輕鬆鬆的,殊不知在今年的考試慘遭重重的滑鐵盧,所以決定痛定思痛開始根據官方提供的評測範圍,一章一節的仔細研讀。
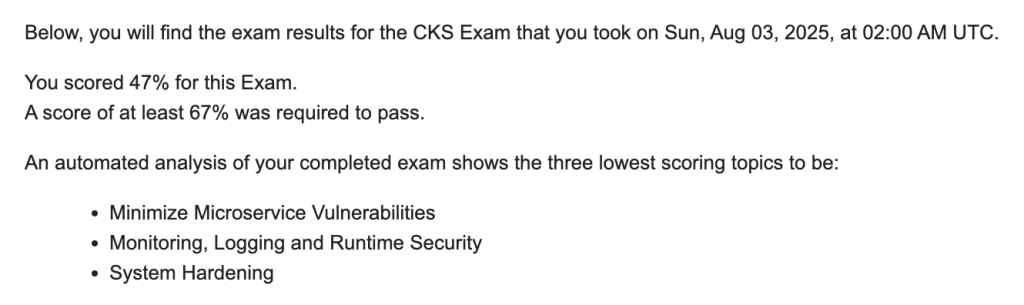
後續會針對官方提出的這些項目一一的研究,希望可以在結束後再創巔峰取得認證。主要會分為以下六個大項:
明天就開始吧
參考資料
Certified Kubernetes Security Specialist (CKS)

感謝 未知作者 的精彩分享!
JavaScript 生態系統真的很豐富,這樣的分享對開發者很有幫助。
也歡迎版主有空參考我的系列文「南桃AI重生記」:https://ithelp.ithome.com.tw/users/20046160/ironman/8311
如果覺得有幫助的話,也歡迎訂閱支持!